Challenges & Best Practices for DevOps Security
Secure your CI/CD pipeline with DevTools DevOps Security — protect every deployment, prevent breaches, and ensure compliance. Book a free consultation today!
14 +
Years of Experience
550 +
Happy Customers
250 +
Years of Tech Leadership Exp.

"License Reseller" and "Consulting & Implementation" Partner

TL;DR
- DevOps security (DevSecOps) integrates security into every phase of the software lifecycle to protect distributed microservices and cloud environments.
- Key challenges include cultural resistance, cloud misconfigurations, container vulnerabilities, and weak secrets or access management.
- Best practices involve embedding DevSecOps governance, automating security checks, managing configurations, and enforcing privileged access controls.
- Proactive, continuous monitoring and collaboration between development, operations, and security teams enable secure, agile software delivery.
DevOps security is crucial as organisations transition from traditional monolithic applications to distributed microservices. This shift requires a change in operational security policies to address the security of multiple micro-systems operating across different levels of the organisation. DevSecOps integrates security considerations at every stage of the development process, ensuring application security.
While DevOps focuses on speedy deployment, the increased use of automation tools, APIs, and cloud containers necessitates strong security measures. DevOps security combines the DevOps landscape with information security policies, marrying the two disciplines.
Unlike the traditional approach of building first and then securing, DevOps security emphasizes securing systems as they are built. However, this introduces the challenge of continuously monitoring systems to identify any vulnerabilities. Balancing security and development requires maintaining system observability.
This article explores the main challenges of implementing DevOps security and suggests best practices to minimize friction between the teams.
What is DevOps Security?
DevOps Security, also known as DevSecOps (DevSecOps refers to a DevOps organisation that is fully integrated with the security organisation), is the convergence of development, operations, and security. It allows businesses to deliver software more quickly while including security into each stage of the SDLC.
DevOps methodologies make it easier to deliver software speedily and more effectively, in small, incremental updates. Applications are created and delivered using a highly automated approach. Applications frequently consist of numerous microservices that are deployed within containers and operated in environments that offer great scalability and resilience in either public or private cloud environments.
However, while DevOps processes, containers and cloud provide important business advantages, they also make application security much more intense. There are many moving elements that need to be monitored and secured as a result of automating application delivery and breaking software into microservices or containers. Each microservice instance serves as a potential attack surface.
A modern DevOps environment also makes use of a wide range of tools, including container orchestrators, image registries, build servers, and code repositories, all of which are vulnerable to hacking. This means that it is impossible to secure applications as an afterthought. It is important to build security into each and every aspect of the environment and application development.
What Are Some DevOps Security Challenges?
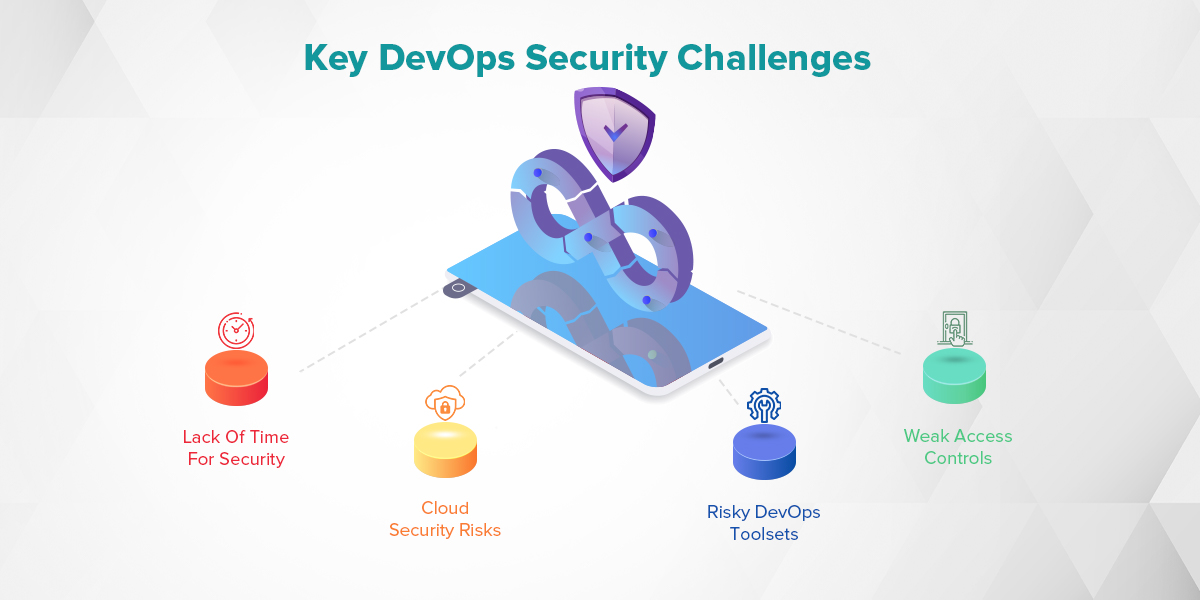
Ensuring smooth integration of security measures into the DevOps pipeline presents a challenge. Here are several common challenges that must be addressed in order to effectively secure your DevOps process:
- Cultural Resistance: Development and operations teams often resist prioritizing security and testing, perceiving them as delays. Security automation can help address this challenge.
- Cloud Security: Cloud adoption introduces new security risks due to the lack of a well-defined network perimeter and the potential for misconfigurations that expose critical resources.
- Containerization: While containers enhance productivity, they also increase the complexity of securing the underlying engine, orchestration, and networking components.
- Collaboration Challenges: Integrating security teams into the DevOps culture can be difficult, as traditional security tools and processes may not align with the rapid, iterative nature of DevOps.
- Secrets Management: Sharing privileged information within DevOps environments requires a robust security strategy to prevent unauthorized access and data breaches.
DevOps Security Best Practices
- Embrace a DevSecOps model: The most important step in safeguarding your DevOps environment is to take this one. Security integration throughout the product development lifecycle (design, development, delivery, operations, and support phases) is necessary for successful DevOps security.
Governance and cybersecurity tools including code review, identity access management, firewalls, configuration, and vulnerability management are all part of the DevSecOps architecture. With DevSecOps in place, you have ‘secure DevOps’ that will no longer create threats and additional costs and gives you seamless delivery. - Enforce policy & governance: Communication & strict policy enforcement are very important in order to achieve the goal of secure DevOps. Bring in transparent cybersecurity policies that are easily understandable and implementable for the teams. This helps teams plan their tasks in line with the set security requirements.
- Automate your DevOps security processes and tools: While you bring in tools and resources, automating them for scaling security features to your DevOps process is important. Automation also minimizes the risk of errors caused by repeating instances and the associated downtime issues.
That will also help you identify potential threats, vulnerable code, and any issues within processes or infrastructure. Automation helps security practises integrate more deeply into the DevOps process chain by overcoming cultural opposition. - Perform comprehensive discovery: While you identify and map issues, it’s equally important to continuously validate all the approved tools, devices and accounts spotted under discovery. Ensure to bring them under security management aligned with your internal policies.
- Conduct vulnerability management: Prior to the product entering production, make sure a strict vulnerability study, assessment, and management is in place. Make sure to conduct vulnerability scans throughout the development and integration phases and well in advance. You can benefit from penetration testing and associated attack techniques.
As products enter the operating environment, DevOps software runs tests and tools against the production environment and infrastructure to address patching-related issues. - Adopt configuration management: Configuration issues are one serious concern that can hit your DevOps workflow. Maintain ongoing configuration checks for all cloud assets across servers and individual builds, and make sure that configuration errors are fixed in accordance with industry best practices.
- Secure access with DevOps secrets management: Ensure to eliminate all credentials embedded in code, files, service accounts and cloud platforms. As a result, you are storing the credentials in a secure location that is central to all processes.
Don’t worry; they can be accessed through privileged password management solutions that call applications and scripts to access passwords if required. Implementing such API calls gives you additional control over code, scripts, and embedded keys. Automate this process to use passwords in line with the policy demands. - Control, monitor, and audit access with privileged access management: The less privileged access rights, the less is the possibility of potential attacks. It’s recommended to secure the privileged account details, eliminate administrator privileges on the end-user side and have a simple workflow that doesn’t demand privileged access.
On the other side, continuously monitor the privileged sessions to ensure they are legitimate and adhere to compliance requirements. Even the least privileged model should limit access to specific production and development systems while granting internal teams the right permissions solely to configure, deploy, build, and handle production issues associated with images they developed.
Make use of privileged access management tools and resources for monitoring and auditing privileged access and credential management. - Segment networks: Reduce the ‘line of sight’ for intruders by organising networks and combining resources like application and resource servers. Create logically cohesive groups from each of them.
Trigger a ‘secure jump server’ with multi-factor authentication and other authorization features to tackle access through a trusted zone. Further, segment access-based context by user, data and application.
Read: What Is DevSecOps? Definition & Understanding How It Works
DevOps vs DevSecOps
The DevOps and DevSecOps may appear to be similar at first glance, with DevSecOps simply incorporating security into the DevOps framework. However, there is a distinction between the two. DevOps, short for development and operations, focus on fostering collaboration between these essential teams throughout the development process. These teams collaborate to establish shared processes, key performance indicators (KPIs), and milestones.
Through this collaboration, the operations team can closely examine the various stages of delivery while incorporating continuous updates and feedback from the development team. DevSecOps is an extension of the DevOps approach, but it goes further by integrating security as an additional layer within the ongoing development and operations process.
Rather than treating security as an afterthought, DevSecOps involves early involvement of Application Security teams to strengthen the development process from a security standpoint and mitigate vulnerabilities.
Conclusion
Securing DevOps lays the path for a full-fledged DevOps implementation with embedded security practices. With security addressed, DevOps is undoubtedly an omnipotent game-changer technology solution for fast-changing business needs.
FAQs
It refers to the integration of development, operations, and security procedures into the software development lifecycle. It also goes by the name DevSecOps. While ensuring the security of applications at every step of development, it helps organizations in delivering software rapidly and effectively.
Conflicting goals between developers and security teams, cloud security risks, risky DevOps toolsets, weak access controls, and a lack of time for security are some of the challenges.
Adopting a DevSecOps model, implementing policy and governance, automating DevOps security processes and tools, and having comprehensive discovery, vulnerability management, configuration management, and secrets management are some of the best practices.
To ensure the security of applications, integrating security into the DevOps environment is important. Besides, in order to prevent potential attacks, security must be incorporated into every part of the environment and in each stage of application development due to the high level of automation and the division of applications into microservices and containers.
DevSecOps is a model that focuses on the importance of communication and collaboration between DevOps and IT teams to prioritize security in the development process. By incorporating security into the development process, DevSecOps helps to prevent major security failures and keep track of potential vulnerabilities early in the process.
DevSecOps works for the communication and collaboration between DevOps and IT teams to prioritize security in the development process. It helps to prevent major security failures and keep track of potential vulnerabilities early in the process by incorporating security into the development process.

Pramodh Kumar M is a Solutions Architect at DevTools with over 6 years of specialized experience in DevSecOps and enterprise IT solutions. He holds multiple advanced certifications, including Certified Kubernetes Security Specialist (CKS), GitHub Advanced Security, and Azure Solutions Architect Expert. Pramodh specializes in Agile, Cloud & DevOps toolchain implementations, with extensive hands-on experience helping enterprises with digital transformation initiatives. His expertise extends to ServiceNow implementation and support. He is passionate about sharing practical insights on Cloud, DevOps, Automation, and modern IT operations.