What Is SAST (Static Application Security Testing)? Benefits, Tools & How It Works
Enhance software security with DevTools Static Application Security Testing — automate analysis, reduce risk, and support secure development practices. Connect with our experts today!
14 +
Years of Experience
550 +
Happy Customers
250 +
Years of Tech Leadership Exp.

"License Reseller" and "Consulting & Implementation" Partner
TL;DR
- SAST scans source code early in the SDLC to identify vulnerabilities without executing the application.
- It offers fast, automated, rule-based analysis but may produce false positives, depend on language support, and require careful setup.
- SAST complements DAST, SCA, and IAST to provide broader coverage, improving detection of issues like injections and insecure coding patterns.
- Popular SAST-related tools include GitHub, Dynatrace, DeepSource, StackHawk, and SonarQube, with DevTools offering additional inspection and debugging support.
What is SAST?
SAST, or Static Application Security Testing, involves scanning the application source code for security flaws without actually running the code. The objective of SAST (Static Application Security Testing) is to find security holes and coding errors that could result in a security breach. This method is frequently applied during the software development process to stop security vulnerabilities from ever being introduced.
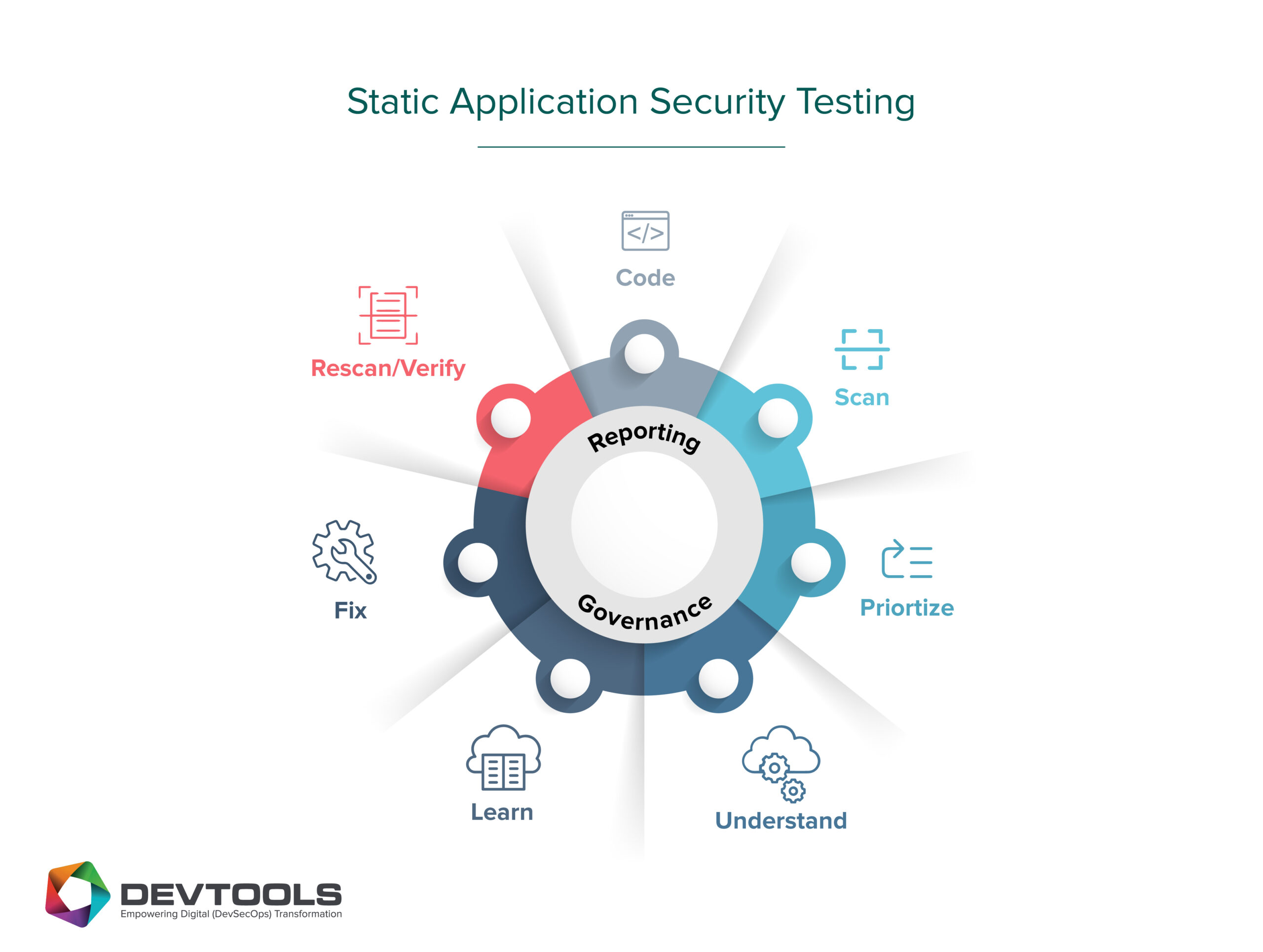
Static Application Security Testing (SAST) Tools: Advantages and Disadvantages
Advantages:
- Early SDLC: It can scan your code even as you are still writing it because it is designed for source code. The SAST Testing application can be plugged into our publicly available IDE. It compares your code to industry standards when you are writing your code, you can use it. The SAST IDE plugins are easily accessible online and just a click away.
- Line of Problem: The fantastic security tool will not only find vulnerabilities for you but also point you to exactly where the problem is so it can be fixed right away.
- Predefined or Defined Rules: SAST applies rules to the source code, unlike the DAST tool, which lets you choose what to test. These rules can be manually configured or automatically applied using the SAST’s predefined rule automation algorithms.
- Non-execution: This security tool does not require the running of the source code to function; it simply requires the static source code. The fact that the SAST scan runs on built code makes it significantly faster than DAST scan.
- Easy automation: Because Static Application Security Testing Is automated, it does not require as many configurations as DAST.
Disadvantages:
- False positives: The high level at which SAST access to the source code captures false positives is one of the main drawbacks. When SAST is used to scan an application’s code, it frequently identifies a line of code as having problems, even though it will eventually be discovered that the assertion was incorrect. Some of the security concerns that have been brought forward may not even be issues or present a threat to the organisation.
- Misplaced Test: Static Application Security Testing occasionally scans the incorrect location while the repair is in another location, which results in false positives most of the time. For instance, unclean user input could have been corrected at the back end, but because the problem has not been resolved at the front end, the tool might mistakenly identify it as a problem because all the application codes are not stored in the same repository.
- Language Dependent: SAST is a language-specific security tool. Its effectiveness is based on the programming language that is employed. If you require a SAST tool, for instance, you should buy the kind that supports the programming language that was used to create your application.
- Getting over one SAST: A single SAST tool might not always be able to identify all the vulnerabilities in an application. Hence, it is sometimes beneficial to have more than one. While one might support multiple languages, another might perform well in extensive testing.
- Difficult Initial Setup: Some developers remark that setting up SAST initially in an agile environment is difficult. It is more important to carefully analyse the kind of SAST you intend to use; it should be a device that will present you with fewer difficulties during setup.
Why is Static Application Security Testing Important?
Developers considerably outnumber security personnel. It might be challenging to locate the resources necessary to perform code reviews on even a small subset of an organisation’s apps. One of the key benefits of SAST tools is their ability to analyse the entire codebase. They are also far quicker than manual secure code reviews carried out by humans. In a couple of minutes, these tools can scan millions of lines of code. SAST tools reliably identify critical flaws, including buffer overflows, SQL injection, cross-site scripting, and others through automatic detection. As a result, using static analysis to the SDLC can greatly raise the overall calibre of the code generated.
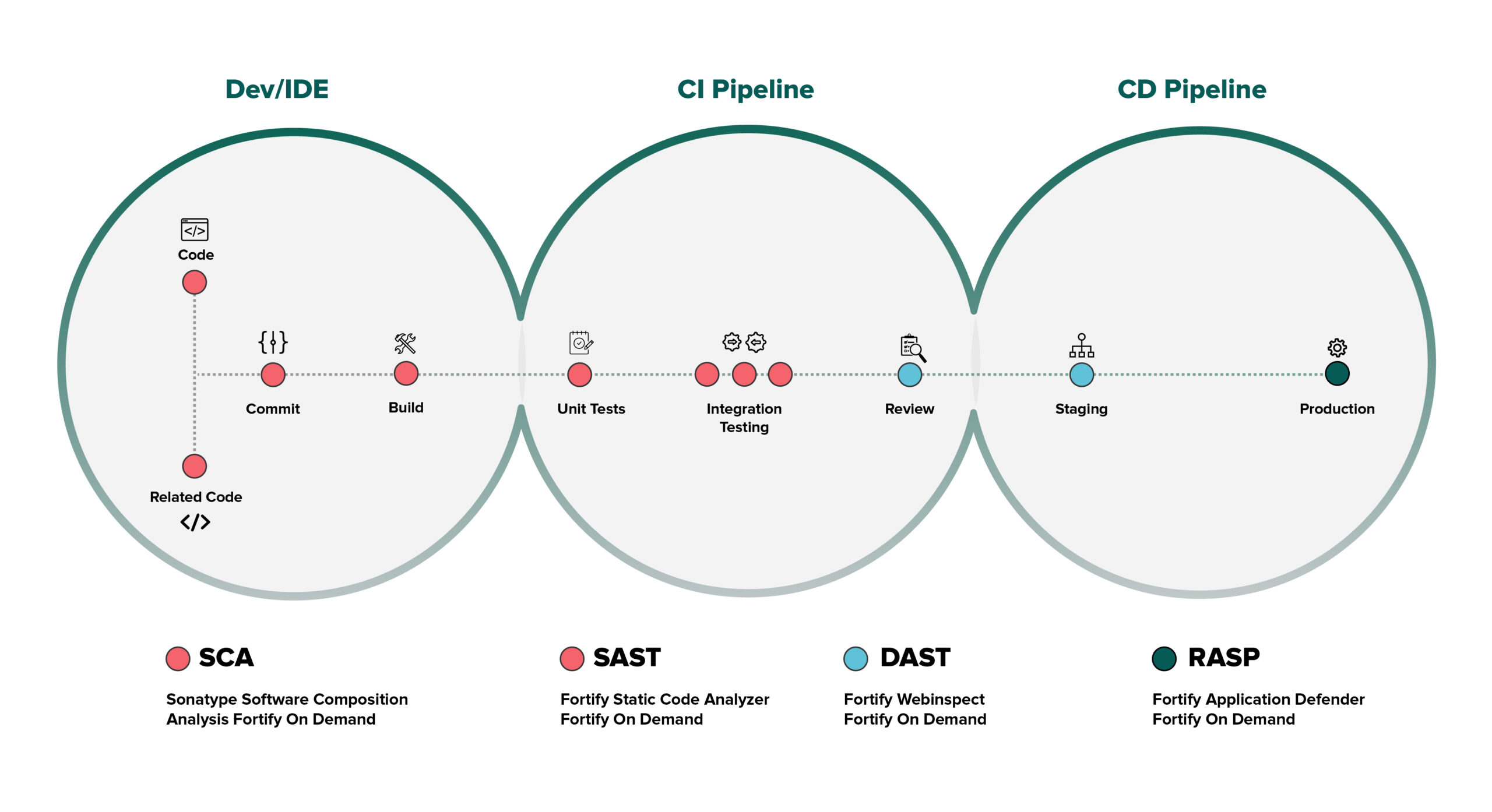
How Does Static Application Security Testing Works?
Static code Analysis is a technology used by SAST that can be compared to a building’s security guard. A static code Analyzer examines the source code to seek for coding and design defects that could allow for malicious code injection, much like a security guard checks for unlocked doors and open windows that could allow entry to an intruder. According to OWASP, some examples of these harmful assaults are SQL Injections, Command Injections, and Server-Side Injections.
What makes SAST Different from Other Security Testing Methods?
In order to interact with the source code, Static Application Security Testing scans it for flaws. DAST, on the other hand, operates solely with inputs and outputs when the application is running without having access to the source code. Both security technologies work best together; a vulnerability that one security tool misses may be found by the other.
When combining SAST with additional security technologies, speed is yet another consideration. For example, DAST takes longer to finish scanning a running application, whereas SAST scanning is quicker when access to the source code, but both will always provide you with the best course of action to fix the problem and increase your application security.
Always intend to utilise a SAST tool from the beginning of the development process, and you can include other tools like IAST and RASP while utilising the DAST tool later, after the code has been built and sent to the staging environment for alpha and beta testing.
Always remember that additional security technologies may subsequently discover any flaws that static application security testing is unable to find quickly.
In what ways does SAST enhance existing application security testing techniques?
Important application security testing types that provide various viewpoints on the security posture of the development lifecycle include SAST, DAST, SCA, and IAST.
Utilising all three of these tools together will provide you with a comprehensive assessment of the security of your application because they complement one another nicely.
Top Static Application Security Testing (SAST) Tools You Should Know
1. GitHub
With the ability to readily follow the history of files in the code repository, GitHub is a tool that significantly facilitates code collaboration. Although GitHub still allows users to upload source code and share it with distant collaborators, it has advanced by incorporating strong security safeguards. By enabling developers to identify and address security issues in their code as they write, GitHub significantly improved its security capabilities.
In essence, teams may detect and fix vulnerabilities using GitHub’s application security before code is integrated into the repositories. Facilitating the integration of security analysis into the development workflow makes left-shift security easier to deploy.
2. Dynatrace
The aim of Dynatrace, which is an application and infrastructure monitoring tool, is to reduce the complexity of the cloud. In order to deploy software more quickly and safely, it makes use of its AI-powered platform to automate DevOps and offer intelligent security.
With Dynatrace, you may have a seamless online experience with a comprehensive view of your computing environment.
3. DeepSource
DeepSource, a powerful static analysis platform that offers Shift Left security technologies of the highest calibre. With its continuous code quality checks, DeepSource focuses on making life simpler for DevSecOps and QA teams.
With DeepSource, you can immediately start analysing code with only a few setups while also carefully monitoring the critical metrics of code health. It goes one step further with its Autoflix feature, which creates bug fixes so that vulnerabilities don’t end up in production, if automatically formatting your code wasn’t enough.
4. StackHawk
For DevSecOps in CI/CD pipelines, StackHawk streamlines and automates application security testing. It is a cutting-edge, dynamic security testing tool designed to find and fix vulnerabilities in code.
StackHawk analyses for security vulnerabilities, whether defects are accidentally inserted into source code or appear from open-source components. Developers are given the tools they need, such as notification and enough context, to triage a problem and find the source of a security fault.
StackHawk integrates with CI/CD pipelines and DevOps platforms, including Jenkins, Travis CI, GitLab, GitHub Actions, CircleCI, Azure Pipelines, BitBucket Pipelines, Atlassian Bamboo, and many more. It also offers API security testing capabilities.
5. SonarQube
SonarQube automates code inspection, giving the developers the tools they need to design safer and cleaner code. Additionally, the ability to provide static code analysis rules facilitates the process of publishing high-quality code.
With support for multi-language applications and a current list of 24 programming languages, SonarQube is flexible and comprehensive. For various languages, including C#, C++, Java, PHP, Python, and others, it provides crucial security. Additionally, it offers code review input by inspecting repository branches during pull requests for platforms like GitHub, BitBucket, GitLab, and others.
To read more and find the best tools along with their features, read our blog on 9 Best SAST Tools For 2025
How Can DevTools Help You In SAST?
Devtools can be helpful in advancing Static Application Security Testing (SAST) initiatives. DevTools, typically available in modern web browsers, provide a range of features and functionalities that can assist developers and security professionals in performing SAST. Here’s how DevTools can help in SAST:
- Code Inspection: Using Devtools, developers can examine and audit a web application’s HTML, CSS, and JavaScript code. Developers can find potential security flaws in the code by looking for unsafe function usage, unsecured data handling, or a lack of input validation.
- Debugger: Devtools have strong debugging features that let programmers step through code set breakpoints and monitor variables and data in real-time. Developers can understand the behaviour of the programme and find security problems by debugging the code.
- Network Monitoring: Devtools provide network monitoring features that enable programmers to examine HTTP requests and replies sent back and forth between the server and the web application. Developers can evaluate the security of data in transit and find potential vulnerabilities by examining network traffic.
- DOM Manipulation: DevTools provide the ability to modify the Document Object Model (DOM) of a web page in real-time. Developers can find security flaws linked to code injection, cross-site scripting (XSS), or unsafe DOM manipulation by modifying the DOM.
- Performance Analysis: DevTools offer performance profiling capabilities, allowing developers to assess the efficiency of their code and identify performance bottlenecks. Developers can improve the application’s overall security posture by analysing and improving code performance.
- Auditing and Reporting: DevTools frequently come with built-in auditing and reporting functions that help identify and address security vulnerabilities. Developers can get real-time feedback on security-related issues and effectively address vulnerabilities by utilising auditing capabilities.
For a comprehensive SAST approach, it is recommended to utilize dedicated SAST tools specifically designed for static code analysis, vulnerability detection, and compliance checking. DevTools can complement these tools by providing a more interactive and dynamic environment for code inspection, debugging, and analysis during development and testing processes.
FAQs
Pros
Early detection of vulnerabilities, Comprehensive coverage, integration into the development process, automation and scalability and compliance with security standards.
Cons
False positives and negatives, limited context, high noise-to-signal ratio, limited support for some languages and frameworks and complex setup and configuration.
Yes, for a comprehensive application security testing strategy, using static application security testing (SAST) tools in addition to dynamic application security testing (DAST) technologies is advised. SAST and DAST are complementary strategies that focus on certain aspects of application security and offer unique benefits.
By assisting businesses in locating and addressing any security flaws in their software applications, static application security testing (SAST) plays a key role in the field of application security (AppSec). Here are some key roles and benefits of SAST in AppSec:
Early detection of vulnerabilities, Secure coding practices, Comprehensive analysis, Integration into the development process, Compliance and security standards and Cost-effective security testing.
Early detection of vulnerabilities, Secure coding practices, Comprehensive analysis, Integration into the development process, Compliance and security standards and Cost-effective security testing.
To avail of these benefits, you need a SAST tool.
SAST tools enhance web application security by detecting vulnerabilities, promoting secure coding practices, providing comprehensive coverage, integrating into the development process, ensuring compliance with security standards, enabling continuous security improvement, and reducing risks and costs associated with security vulnerabilities.

Pramodh Kumar M is a Solutions Architect at DevTools with over 6 years of specialized experience in DevSecOps and enterprise IT solutions. He holds multiple advanced certifications, including Certified Kubernetes Security Specialist (CKS), GitHub Advanced Security, and Azure Solutions Architect Expert. Pramodh specializes in Agile, Cloud & DevOps toolchain implementations, with extensive hands-on experience helping enterprises with digital transformation initiatives. His expertise extends to ServiceNow implementation and support. He is passionate about sharing practical insights on Cloud, DevOps, Automation, and modern IT operations.