Dynamic Application Security Testing- DAST Basics

What is DAST ?
Dynamic application Security Testing (DAST) is an application security testing technique that involves examining an application in its running phase without any prior knowledge of its internal interactions or system-level designs. They have no access or visibility into the source program.
This “black box” testing approach analyses the application from an external perspective, observes its running state, and evaluates its responses to simulated attacks conducted by a testing tool. The application’s reactions to these simulations help in assessing its vulnerability and potential susceptibility to real malicious attacks.
How Does DAST Work?
DAST tools launch automated scans that simulate malicious external attacks on the application. The objective is to identify unexpected outcomes. For instance, a test is potent to inject malicious data to uncover injection vulnerabilities.
Typically, a DAST tools examines HTML and HTTP access points to discover threats with tests that emulates random user behaviours & actions.
The emerging new generation of DAST solutions harnesses the power of AI to address the challenges associated with conventional DAST:
- The next-generation DAST automatically develops test sets and dynamically detects the underlying application’s structure, eliminating the need for manual tuning.
- It leverages machine learning algorithms and fuzz testing to analyse discoveries similar to a human penetration tester, assessing if they are genuine threats or not, hence removing false positives.
- It accesses web applications like a genuine user, trying different control flows until it finds a user interface path that discloses security weaknesses, thereby detecting business logic threats.
- DAST testing utilises AI detection abilities and real-time data from other platform users to detect zero-day attacks, unlike previous DAST, which could only detect familiar threats from updated lists.
Moreover, it offers sophisticated reporting options and compliance audits comparable to those produced by human testers.
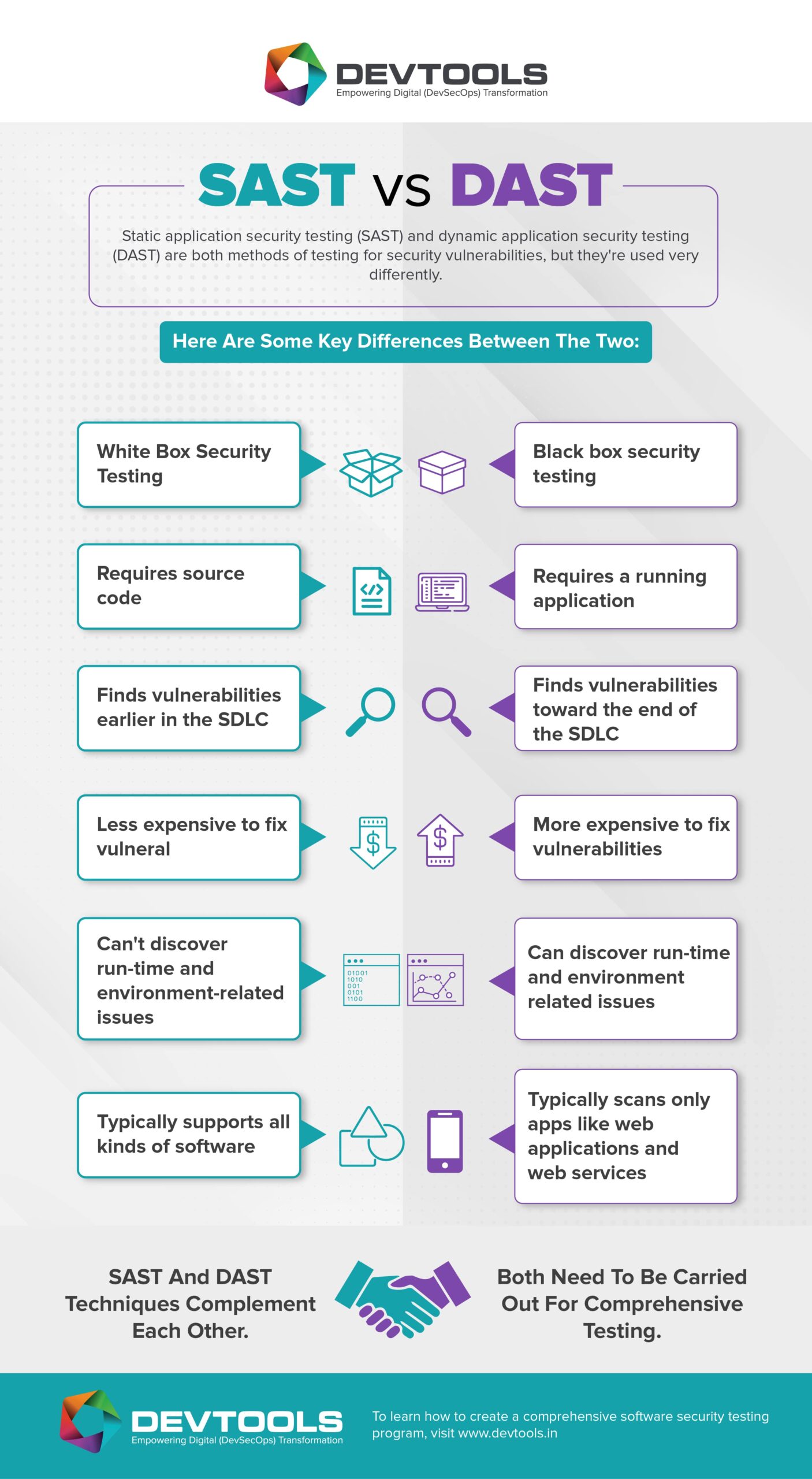
Difference between SAST & DAST
Pros & Cons of Dynamic Application Security Testing
The main function of DAST tools is to test an application while running. The nature of these tools offers numerous benefits while having certain drawbacks. Let’s dig deep to help you assess their suitability for your software project.
Pros:
- Fewer false positives: DAST typically generates fewer positives as compared to SAST, as it doesn’t scan the entire application. This enables faster threat verification and the opportunity to assess preventive measures.
- Language agnostic: Unlike other security testing techniques, it is independent of programming languages. This is what makes it unique. It ignores source code, bytecode, and assembly code in favour of examining system inputs and outputs. If your software uses a specialised programming language, DAST can be your only practical testing option.
- Quick retest of fixed vulnerabilities: By automating the replication of security flaws and incorporating them into the test suite, DAST efficiently controls regressions. This makes sure that all upcoming releases contain the interactions that caused problems in the past. As a result, if these issues return, DAST recognises them and stops them before they are broadcast.
Cons:
- No code insights: DAST only focuses on your system’s inputs and outputs. This makes it difficult to connect particular lines of code to threats found.
- Slower testing process: The need to execute and interact with the software can introduce delays in the process, even when using automated testing methods. Going through a signup process with various input combinations takes significant time.
- Results late in CI/CD pipeline: Due to the reliance of DAST on the application execution for testing, DAST is positioned at the right of your CI/CD pipeline. This might take considerable time, especially when dealing with older, complicated, and large-scale applications.
- Manual testing may be required: The incorporation of DAST in your CI/CD pipeline becomes impracticable in situations where automating the execution and usage of your application is not possible, mandating human testing of the application for each release.
What problems does DAST solve?
Applications power the global economy, and as our digital world develops faster, organisations are under tremendous pressure to keep ahead of the curve. In a world where highly-skilled, persistent threat actors are ready to take advantage of any opportunity to disrupt, endanger key data, and cause harm, businesses must continually innovate.
It is vital to create and carry out a plan to guarantee their application to successfully navigate the new world.
Furthermore, Dynamic Application Security Testing tools operate through the simulation of automated attacks on an application, emulating the actions of a malicious attacker. The objective is to identify unexpected outcomes or results that might potentially be exploited by attackers to compromise the application.
As DAST tools lack internal information regarding the application or its source code, they approach the attack with a similar level of knowledge and understanding as an external threat actor would possess.
Why are Dynamic Application Security Testing tools vital to application security?
The role of DAST tools in automating the assessment, analysis and documentation of security threats is vital. They are an integral part of the DevSecOps initiative, which aims to proactively integrate security measures throughout the software development lifecycle (SDLC) by including security scans at every stage.
DAST tools are typically categorised into four main types:
- Static application security testing (SAST) – provides white-box testing, which analyses the source code while its components are at rest.
- Dynamic application security testing (DAST) – simulates external attacks on applications using black-box testing.
- Interactive application security testing (IAST) – helps with the instrumentation of the
application code. The objective is to detect and report issues during runtime. - Software composition analysis (SCA) – scans the code and analyses open-source software components, searching for threats and checking license compliance.
What are Comprehensive and Usable Application Security Solutions required?
With businesses’ increasing reliance on web and mobile applications, data breaches have significantly increased due to application security threats. Consequently, it has become critical for organisations to prioritise their applications’ security and code.
Challenges that organizations are currently facing:
- The adoption of cloud and cloud-native application technologies is contributing to increased complexity of applications.
- The widespread use of massively distributed microservices and serverless functions results in developers being solely focused on their individual services. This has led to a lack of comprehensive understanding of the entire codebase.
- The proliferation of applications contributes to an exponential growth in the volume of software code deployed to the cloud. Hence, it expands the potential attack surface.
- As organisations undergo digital transformation, the understanding of legacy code is diminishing due to the retirement or role switches of developers.
- The prevalence of third-party and open-source software contributes to increased application complexity. It is due to the substantial portion of the application code being developed externally to the organisation’s purview.
- DevOps methodologies enable faster development timelines while limiting resource availability for manual or outdated security checks.
The acceleration of code changes, the evolving hosting architecture of applications, and the increasing frequency of application security solutions that are also highly usable. These solutions should meet the requirements of both information security and application development teams in terms of collaboration.
They should operate efficiently within the project context, providing precise reports on threats and application security status. They should also provide developer education through expert consultation for complex issues, as well as seamless integration into software development life cycle (SDLC).
Additionally, the implementation of Dynamic Application Security Testing tools is crucial to determine the security status of in-production applications and user interaction. Additionally, it has become critical for teams to adapt to the evolving nature of applications and adversary tactics.
To achieve effective DevSecOps practices, it is important to incorporate DAST insights into DevSecOps tools. Finally, DAST is critical in identifying actual threats that pose a danger to an organisation and its end users.
- Protect your applications and your code
- Identify inherited and new vulnerabilities
- Assess vulnerabilities to expedite remediation
Conclusion
With organisations’ greater reliance on cloud platforms, it is important that they address security concerns thoroughly, including the application security layer. The constant emergence of new applications, APIs, and functionalities expands the application attack surface significantly.
This expansion incents malicious actors to exploit known vulnerabilities or vulnerable code with readily available tools and utilities. Once an application is compromised, these actors can gain unauthorised access to sensitive customer data, personally identifiable information, and other valuable corporate assets, resulting in costly data breaches and customer trust erosion.
During the development phase, relying solely on application testing is insufficient to protect applications from potential breaches in production. Implementing a formal application security programme is critical for effectively mitigating overall business risk.
Organisations can identify potential exploits that could be used in application attacks by implementing the appropriate strategy and technology while also providing guidance on how to proactively protect applications before any breach occurs. This approach empowers teams to take responsibility and address potential issues quickly and without causing disruptions.
FAQs
It actively scans and tests applications for vulnerabilities and security threats, helping to identify potential risks and mitigate them effectively.
To effectively scan, identify, and address vulnerabilities in applications ensuring comprehensive security coverage and minimised risks.
By conducting dynamic scans and tests to identify vulnerabilities, assess security weaknesses, and provide actionable insights for remediation.