What Is DevSecOps? Definition & Understanding How It Works
Transform software delivery using DevSecOps by DevTools to enhance resilience, automate compliance, and accelerate releases. Schedule a callback for a free consultation!
14 +
Years of Experience
550 +
Happy Customers
250 +
Years of Tech Leadership Exp.

"License Reseller" and "Consulting & Implementation" Partner

TL;DR
- DevSecOps embeds security throughout the SDLC, shifting left and enabling early, cost-effective vulnerability detection.
- It strengthens collaboration between development, operations, and security teams while maintaining delivery speed.
- Key benefits include proactive security, faster patching, automation-ready workflows, and consistent, repeatable processes.
- Challenges include cultural adoption, limited visibility, tool integration, multi-cloud complexity, and partial automation limits.
What is DevSecOps?
DevSecOps, short for “development, security, and operations,” is a modern software development approach that embeds security into every phase of the software development lifecycle (SDLC). Instead of treating security as a final step, DevSecOps ensures continuous security testing, automation, and collaboration across teams. By making security a shared responsibility, it helps organizations deliver faster, more reliable, and secure applications while minimizing vulnerabilities.
By integrating security into the continuous integration and continuous delivery (CI/CD) pipeline, DevSecOps enables development teams to tackle critical security issues with the same efficiency and speed as DevOps. This proactive approach ensures vulnerabilities are identified and resolved early, preventing costly delays and strengthening overall resilience.
In the past, security was often addressed at the end of the development cycle. However, with the rise of sophisticated cyber threats and accelerated release cycles, DevSecOps has become the preferred method for ensuring application security in today’s fast-paced development environment.
Why is DevSecOps Important?
DevSecOps is important because it integrates security into every stage of the software development lifecycle, making it a shared responsibility across development, security, and operations teams. By shifting security left, vulnerabilities are identified early, reducing the cost and complexity of fixes while accelerating delivery. This proactive approach protects organizations against misconfigurations, exploits, and evolving cyber threats. DevSecOps not only strengthens compliance and resilience but also ensures faster release cycles, improved collaboration, and more secure software products.
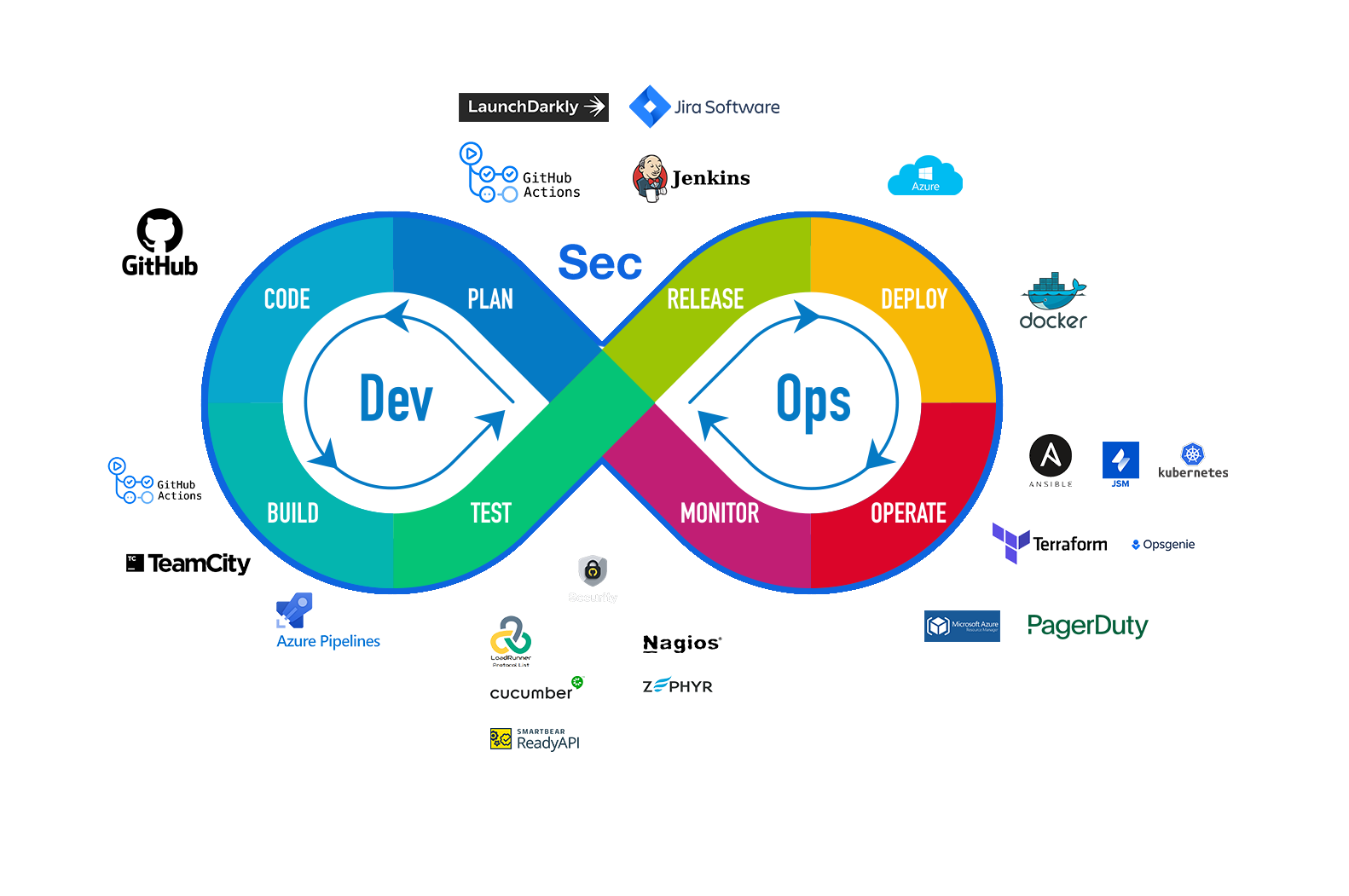
How Does DevSecOps Works?
DevSecOps aims to equip development teams with a complete security framework. This is accomplished by fostering ongoing collaboration between development, release management (also called operations), and the security team of an organization. This collaborative approach is emphasized at every stage of the CI/CD Pipeline.
The CI/CD Pipeline consists of six stages: Code, Build, Store, Prep, Deploy, and Run. Each stage is described below to highlight the advantages of integrating security early in the process.
Code: The initial step in adopting a DevSecOps development approach is to write code in secure and trusted segments. VMware Tanzu® provides tools that regularly update these inherently secure building blocks, ensuring better protection for your data and applications from the beginning.
Build: The initial step in adopting a DevSecOps development approach is to write code in secure and trusted segments. VMware Tanzu® provides tools that regularly update these inherently secure building blocks, ensuring better protection for your data and applications from the beginning
Store: In today’s dynamic cybersecurity landscape, any off-the-shelf technology stack poses a potential risk. Therefore, it is crucial to continuously assess each off-the-shelf application or backend service. Thankfully, with VMware, developers can securely pull opinionated dependencies using VMware Tanzu and scan container images for vulnerabilities with VMware Carbon Black Cloud Container™.
Prep: Before deployment, organizations must ensure that their applications comply with security policies. VMware Tanzu and Carbon Black Cloud Container can validate configurations against the organization’s security policies before proceeding to subsequent stages of the development cycle. These configurations define how the workload should operate, providing valuable insights into potential vulnerabilities and setting the stage for a successful deployment in the CI/CD pipeline.
Deploy: The scans conducted in previous steps provide organizations with a comprehensive understanding of the application’s security status. Identified vulnerabilities or misconfigurations in the development process are presented clearly, allowing organizations to address issues and establish stronger security standards to enhance their security posture.
Run: During the deployment phase, SecOps teams can leverage active deployment analytics, monitoring, and automation to ensure continuous compliance while mitigating the risk of post-deployment vulnerabilities.
What are the benefits of DevSecOps?
DevSecOps is a methodology that focuses on integrating security into the software development process from the beginning. The benefits of DevSecOps are two-fold: speed and security. DevSecOps allows development teams to deliver better and more secure code at a faster pace and at a reduced cost.
- Rapid, Cost-Effective Software Delivery : Addressing security issues in a typical software development environment can prove to be a time-intensive and expensive task. DevSecOps addresses security concerns early on, minimizing the need for repeated processes to address security issues later. Integrated security also cuts out duplicative unnecessary rebuilds and reviews, resulting in more secure code.
- Improved, Proactive Security : DevSecOps introduces cybersecurity processes from the initial stage of the development cycle. The software development process is altogether taken to review, audit, scan and test the code for any potential security vulnerabilities. By utilizing this approach, security issues are detected and addressed promptly, resulting in reduced expenses in fixing them. Better collaboration between security, development, and operations teams also improves an organization’s response to incidents and problems when they occur.
- Accelerated Security Vulnerability Patching : One of the main benefits of DevSecOps is the ability to quickly manage newly identified security vulnerabilities. As DevSecOps integrates vulnerability scanning & the ability to identify, patching into the release cycle, and patch common vulnerabilities & exposures (CVE) is diminished. This limits the window a threat actor has to take the advantage of vulnerabilities in public facing production systems.
- Automation Compatible with Modern Development : Automation of security checks is strongly dependent on the project and organizational goals. However, if an organization uses a continuous integration/continuous delivery pipeline to ship their software, cybersecurity testing can be merged into an automated test suite for operations teams. Automated testing can ensure that incorporated software dependencies are at appropriate patch levels and that software passes security unit testing.
- A Repeatable and Adaptive Process : DevSecOps lends itself to repeatable & adaptive processes. This approach ensures security is applied consistently across the environment, as the environment changes & adapts to new requirements. A mature implementation of DevSecOps will have configuration management, a solid automation, immutable infrastructure, containers, orchestration, and even serverless compute environments.
What are the differences between DevOps & DevSecOps?
Modern software development relies on an agile-based SDLC to speed up the development and delivery of software releases, updates, and fixes. While DevOps and DevSecOps both use the agile framework, they have different objectives. DevOps aims to accelerate the delivery of applications, whereas DevSecOps focuses on delivering apps that are as secure as possible, as quickly as possible.
The primary goal of DevSecOps is to promote the rapid development of a secure codebase. This requires integrating security into every part of the software development life cycle (SDLC), from build to production. In DevSecOps, security is a shared responsibility of all stakeholders in the DevOps value chain. Collaboration between development, release management, and security teams is crucial.
Overall, DevOps prioritizes speed, while DevSecOps maintains velocity without compromising security. By embracing DevSecOps, organizations can deliver secure software quickly, efficiently, and effectively.
In conclusion, while DevSecOps integrates security into the software development process, DevOps betters software delivery, quality and speed. Including DevOps security considerations throughout the software development lifecycle, DevSecOps is a subset of DevOps.
What are the challenges of DevSecOps?
DevSecOps can present several challenges for organisations, some of which include the following:
- Collaboration Among The Team : The first challenge is convincing people to adopt the new DevSecOps way of doing things. In most organizations, the team members are habitual to old way of working & hence it takes time to change their way of thinking. Seminars and training can help ease the transition.
- Limited Visibility : Traditional DevOps practices focus on speed, but incorporating security tests at all stages of the SDLC inevitably slows down the process. Teams must make wise decisions to balance speed and security.
- Tool Integration and Documentation : Working with existing toolsets and integrating security tools into the existing business practice is challenging. Creating better documentation can help teams refer back and integrate tools more efficiently.
- Multi-Cloud Environment : Securing resources in a multi-cloud environment is a complicated task. Focusing on data security and adopting hybrid lifecycles can help overcome this challenge.
- Cannot Fully Automate : Most DevOps practices are automated to get faster releases. However, when security practices are incorporated, they often require human input, which slows down the process.
What are the best practices of DevSecOps?
In today’s rapidly evolving digital landscape, companies are increasingly adopting DevSecOps as a key strategy to ensure the security of their applications.
- Shift left: This is a crucial aspect of DevSecOps. It involves checking for vulnerabilities in the early stages of software development. By incorporating security at the beginning of the development process, software teams can prevent undetected security issues from arising later on. This approach emphasizes the importance of creating secure code in a DevSecOps process.
- Shift right : It refers to focusing on security after the application has been deployed. Even though security checks are performed earlier, some vulnerabilities might still go unnoticed and become apparent only when customers use the software. This approach highlights the importance of continuous monitoring and addressing security issues as they arise.
- Automated Security Tools : Using these tools, DevSecOps teams need to make multiple revisions in a day to keep up with the rapid pace of software development. Automated security tools, integrated into the CI/CD process, can help prevent security evaluations from slowing down development. This approach allows for continuous and efficient monitoring of security issues throughout the development process.
- Promote Security Awareness : Companies must prioritize security awareness and make it a core value when building software. All team members involved in developing applications must share the responsibility of protecting software users from security threats. By promoting a culture of security, companies can ensure that everyone involved in the development process is aware of the importance of maintaining secure code and addressing security issues promptly.
Streamlining Security With DevSecOps: Incorporating Into The CI/CD Pipeline
DevSecOps is an approach that ensures the implementation of security measures at every stage of the application software development life cycle (SDLC). This is achieved by incorporating the necessary security checks into the CI/CD automation process using suitable tools.
FAQs
– Early Security Integration
By including security considerations earlier in the SDLC, DevSecOps enables developers to catch and fix vulnerabilities before they reach production or post-release. This approach results in cost savings and enhances the overall software security posture.
– Industry-Specific Benefits
Automotive industry- Reduced cycle times while meeting standards like MISRA and AUTOSAR.
Healthcare Industry- enables digital transformation while ensuring patient data privacy.
Financial/retail/e-commerce sectors- addresses OWASP Top 10 security risks and maintains PCI DSS compliance.
– Secure Code Writing
It helps developers create secure code minimizing CWE Top 25 most dangerous software errors. This is especially crucial for embedded, networked, dedicated, consumer, and IoT devices, where a single software vulnerability can have significant consequences.
DevSecOps integrates and security practices throughout the software development lifecycle, combining development, security, and operations. It reduces software vulnerabilities and cyber-attacks by integrating an automating security from development to deployment.
DevSecOps is a combination of both cybersecurity & DevOps. DevSecOps integrates security into the software development lifecycle, while cybersecurity encompasses a broader range of domains. DevSecOps is a subset of cybersecurity, focusing on security measures during software development.
Yes, DevSecOps does require coding skills. To effectively implement security measures into the software development lifecycle, DevSecOps engineers must have a strong understanding of programming languages and code development.
DevSecOps tools are software solutions that integrate security practices into the software development cycle, enabling developers to detect and fic security threats throughout the process.
Some DevSecOps Tools Includes:
– Static Application Security Testing (SAST)
SAST tools scan custom code for design flaws and coding errors that could result in exploitable weaknesses. They are primarily used during the code, build, and development phases of the SDLC.
– Software Composition Analysis (SCA)
Software Composition Analysis tools scan source code and binaries, detecting vulnerabilities in open-source and third-party components. They provide insight into security, license risks and can be integrated seamlessly into a CI/CD process to continue vulnerability detection.
– Interactive Application Security Testing (IAST)
IAST tools analyse web application runtime behaviour in the background during manual or automated functional tests. They detect runtime vulnerabilities and provide detailed insights to developers down to the line of code where they occur.
– Dynamic Application Security Testing (DAST)
DAST imitates hacker interaction with a web application/API. It doesn’t require source code access and identify vulnerabilities with low false positives rates. They test applications over a network connection by examining the client-side application rendering.
Implementing DevSecOps requires gradually integrating security into every stage of the DevOps workflow. Start by embedding threat modeling and automated security checks during planning and code commits. Use continuous integration with dependency scanning, role-based access, and security testing throughout builds. In production, conduct penetration tests and maintain continuous monitoring to detect vulnerabilities. This step-by-step approach ensures security becomes an integral part of development without slowing down delivery.

Pramodh Kumar M is a Solutions Architect at DevTools with over 6 years of specialized experience in DevSecOps and enterprise IT solutions. He holds multiple advanced certifications, including Certified Kubernetes Security Specialist (CKS), GitHub Advanced Security, and Azure Solutions Architect Expert. Pramodh specializes in Agile, Cloud & DevOps toolchain implementations, with extensive hands-on experience helping enterprises with digital transformation initiatives. His expertise extends to ServiceNow implementation and support. He is passionate about sharing practical insights on Cloud, DevOps, Automation, and modern IT operations.